
3 Hats a hacker might wear
While not always accurate in its portrayal of hackers, Hollywood does get at least one thing right: there are many types of hackers out there,
Learn more about what we do and how we help companies just like yours!

While not always accurate in its portrayal of hackers, Hollywood does get at least one thing right: there are many types of hackers out there,

Patrick Lencioni’s book, The Five Dysfunctions of a Team, clearly shows that Trust is the basis for developing high performing teams. Until this is addressed,

Did you recently buy a new Mac, but are unsure about what to do with important files in your Windows PC? They don’t have to

We all want to be more productive. Business gurus emphasize the importance of time management and taking breaks to avoid burnout. But aside from motivating

Microsoft’s Office 365 Workplace Analytics gives teams a better perspective and control over their members’ productivity. Using the data gathered by the tool, managers can

Identifying opportunities in all areas of business is vital for growth. However, one area that’s often overlooked is technology. Although it’s tempting to adopt an

Ever powered up a brand new laptop straight out of the box and realized that there are already a ton of apps installed that you

As cybersecurity incidents become more sophisticated, frequent, and intelligent, experts predict that the global market for cybersecurity products in 2020 will exceed that of last

Don’t be so quick to dump that old computer! Despite being slow and clunky, your old desktop or laptop may still add value to your

Microsoft Excel is now better than ever, thanks to its extremely user-friendly features. Pull yourself up skillswise by following our three tips below. Take advantage

Technology has always helped business growth. However, with the many innovations available, knowing which to adopt can be bewildering. Virtual reality (VR) is one technology

Having problems with your Windows 10 updates? Perhaps they’re incompatible with your latest driver update. To prevent such issues from happening, Microsoft has changed the

Some hackers have become so skilled that they don’t even need you to give up your credentials to hack into your account. One recent cyberthreat

Some Mac users have been using their devices for years without learning many of the most useful keyboard shortcuts. That’s fine, but knowing these shortcuts

Today, Wi-Fi isn’t only crucial for your employees to get work done; it’s also a necessary amenity for your office guests. But there’s a right

Today marks the last day that Microsoft will provide updates for the Windows 7 operating system. Depending on who you talk to, your computer may

Surface is comprised of Microsoft’s top-of-the-line laptops and tablets built with touchscreen capabilities, allowing them to integrate with Office 365 in even more efficient ways
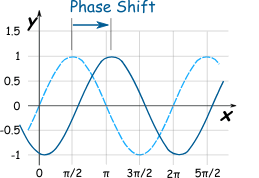
If your business and technology planning are out of sync, it may be time for a technology phase shift. Fortunately technology capability is not cumulative,

To defend against cyberthreats, businesses often implement strong antivirus software and firewalls — but both these solutions are not enough. A cutting-edge identity and access
Microsoft has introduced a convenient and personal way to sign in to your Windows 10 devices. With Windows Hello, you can now log in with

In the healthcare industry, 58% of security incidents begin with an inappropriate action carried out by someone within the affected organization. Although the percentage isn’t

Managing your print infrastructure efficiently is a quick and easy way to minimize your IT budget. Many small and large enterprises don’t realize that they

Microsoft’s Office 365 has made everyday business operations more efficient with programs like Word, PowerPoint, Excel, OneNote, and Outlook. As if that’s not enough, it

Unforeseen disasters can strike at any time, and when they do, your business could come to a grinding halt. Having a business continuity plan could

Sophos researchers are warning Windows 10 users about a new type of malware that can disable and bypass computers’ security software. Known as Snatch, this

Businesses should take every precaution when it comes to data and network protection. Leverage the capabilities of a competent IT partner by augmenting their round-the-clock

The DIY (do it yourself) movement has taken off with the advent of social media. Pinterest runs an entire business off of it! The two

Have you been recently experiencing problems on your Mac computer? Are you wondering if you should shell out some cash for a new one or

A strong network enables your business to surf the web and access cloud productivity apps. Behind these networks are Wi-Fi routers that keep your devices
The phrase “make your own luck” is thrown around a lot by many successful business people, but what does it actually mean? Part of it

If you’ve managed to convince yourself that only large enterprises have the money to take advantage of Business Intelligence (BI), then think again. In the

With the Windows 10 November 2019 Update, your desktop or laptop will get some small but important tweaks to its systems. If you haven’t already,

The bring your own device (BYOD) phenomenon continues to rise in the workplace. There are a number of benefits and risks that BYOD brings. For

Microsoft Teams is fast becoming the go-to application for managing communication and information flow within organizations. We wrote HERE about how Teams will be supplanting

Hyperconvergence isn’t something only large enterprises can benefit from — businesses of all sizes should consider this infrastructure strategy. Read on to learn more about

Whenever a new strain of ransomware is discovered, Mac users are barely affected by the news. But there are rare occasions where ransomware specifically targets

There’s a computer in almost every home and office nowadays. A typical desktop that’s switched on 24/7 for a whole year releases carbon dioxide equivalent

Small- to medium-sized business owners and managers lead busy lives. There’s always one task or another that needs their attention ASAP. Thanks to Google Tasks,

Microsoft is working hard to ensure that its popular cloud-based productivity suite Office 365 is constantly being improved. Because of the great products and support

However good you are at running your business, you won’t get very far without a steady stream of customers. To effectively foster customer relationships, many

The Windows operating system (OS) tends to accumulate all sorts of files to help it complete data processes. However, once those processes are done, no-longer-to-be-used

It is time to shift your focus from managing devices to managing your data. The threat landscape changes quickly but the target remains the same,

As the number of cybersecurity threats increases, many business owners have no recourse but make cybersecurity a priority. But how does one know if your

Knowing which technology to use and when to use it is key to boosting productivity and reducing costs. One of the best ways to do

Confidential data stored in your Mac is at risk of exposure if you leave your desk with your computer on. One of the most effective

Mobile devices are a popular tool for many employees, most of whom will at some point use their personal device for a work-oriented task. Companies

Within Office 365 Groups, there’s a feature called Connectors. It allows you to link to popular third-party services without ever having to leave Outlook. This

Business continuity plans are designed to protect an organization’s critical data in case of a crisis, but employees are also a part of that equation.

Windows 10 is full of useful features, and more are added every time Microsoft releases an update. If it’s been a while since you’ve familiarized

Don’t give your customers any reason to feel insecure when dealing with you. When they visit and use your website, you must engender feelings of